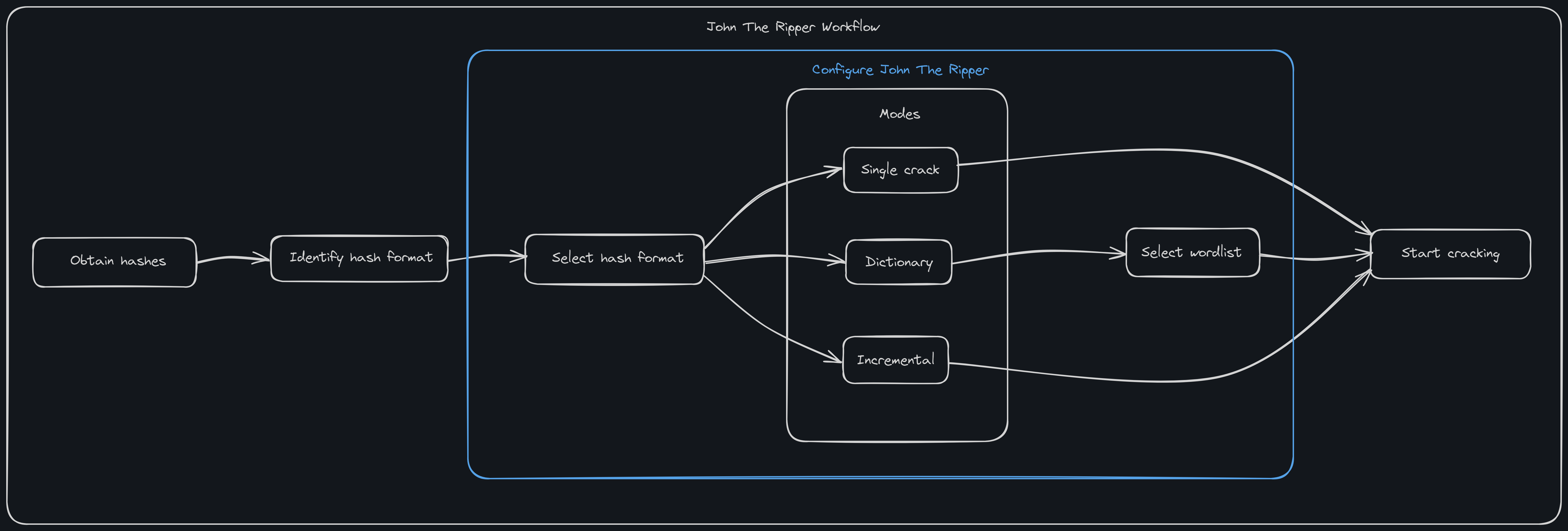
John The Ripper
John The Ripper is mainly used for password cracking. There are also several tools within its suite to help with cracking a wide range of passwords.
The following tools will be covered in this note:
- Overview
- Unshadow
- ZIP2John, RAR2John, SSH2John
- Modes
- Single Crack Mode
- Dictionary Mode
- Incremental Mode
Overview
The base command usage for John The Ripper is:
john --wordlist=/word/list/path --format=Format FileToCrack
Command breakdown:
--wordlist=/word/list/path- Specifies the wordlist to use.--format=Format- Specifies the hash of the password to crack.FileToCrack- Specifies the file which contains the password to crack.
An example will be:
john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5 Hash.txt
Command breakdown:
--wordlist=/usr/share/wordlists/rockyou.txt- Specifies the wordlist to use.--format=raw-md5- Specifies the hash format. In this example, md5.Hash.txt- Specifies the file that the hash to cracked is saved to.
Unshadow
John The Ripper is also able to crack passwords from the "/etc/shadow" file. To do this, we will need to use unshadow and combine it with the "/etc/passwd" file.
Command example:
unshadow passwd/file/here shadow/file/here > output.txt
Command breakdown:
passwd/file/here- The path of where the /etc/passwd file is saved to.shadow/file/here- The path of where the /etc/shadow file is saved to.> output.txt- Tells unshadow on where to save the output to.
Example usage:
unshadow local_passwd local_shadow > crackme.txt
Command breakdown:
local_passwd- The contents of /etc/passwd from the target machine.local_shadow- The contents of /etc/shadow from the target machine.> crackme.txt- The file that we want unshadow to save to.
Note: When using unshadow, we can either use the entire /etc/passwd and /etc/shadow file or just the relevant lines from each file.
Once done, we can use John The Ripper to crack the password. An example will be:
john --wordlist=/usr/share/wordlists/rockyou.txt crackme.txt
Zip2John, Rar2John, and SSH2John
To crack password protected zip files or SSH keys, we can use zip2john for password protected zip files, rar2john for password protected WinRAR files, and ssh2john for SSH keys.
The command format for all 3 tools will be similar. An example will be:
COMMAND file_name.txt > output_file.txt
Command breakdown:
COMMAND- Use either zip2john, ssh2john, or rar2john.file_name.txt- The password protected/SSH key file you wish to crack.output_file.txt- Specifies where to save the output to.
Example usage for zip2john, rar2john, and ssh2john:
zip2john zipfile > zip-out.txt
rar2john rarfile > rar-out.txt
ssh2john id_rsa > ssh-out.txt
Command breakdown:
zipfile/rarfile/id_rsa- Specifies the file you wish to crack. Note that for SSH, it will be the id_rsa file.zip-out.txt/rar-out.txt/ssh-out.txt- Specifies the output file.
Once done, we can use John The Ripper to crack password. An example will be:
john --wordlist=/usr/share/wordlists/rockyou.txt zip-out.txt
John The Ripper also supports more file types:
- pdf2john - PDF
- mscash2john - MS Cash
- keychain2john - OS X keychain
- pfx2john - PKCS#12
- truecrypt_volume2john - TrueCrypt Volumes
- keepass2john - KeePass databases
- vncpcap2john - VNC PCAP
- putty2john - PuTTY private keys
- hccap2john - WPA/WPA2 handshake captures
- office2john - MS Office documents
- wpa2john WPA/WPA2 handshakes
Modes
There are 3 main modes that can be used to crack a password. The modes are:
- Single Crack
- Dictionary
- Incremental
Single Crack Mode
Single crack mode example usage:
john --single --format=FORMAT file_to_crack.txt
Command breakdown:
--single- Tells John The Ripper to use single crack mode.--format=FORMAT- Specifies the hash format.file_to_crack.txt- Specifies the file that contains the password to crack.
Using single crack mode, John The Ripper takes a string and generates variations of that string in order to generate a set of passwords.
For example, if the username is "lone" and the password is "LoNe", we can use single crack mode to generate password variations from the username. This is useful if we have the password hash and know that the password is a variation of the username.
An example will be:
Lone lOne loNe LONE ...and so on
To use single crack mode, first save a file with the username and password hash (md5 in this example) in it. In this example file name is called crack.txt and the contents will be:
lone:e2e8f0bc2c1ec1de7ee50fbae3bfbd0f
Once done, we can use the following command:
john --single --format=raw-md5 crack.txt
Command breakdown:
--single- Tells John The Ripper to use single crack mode.--format=raw-md5- Specifies the format to be md5.crack.txt- Specifies the file that contains the hash to crack.
Dictionary Mode
Dictionary mode example usage:
john --wordlist=/word/list/path --format=Format FileToCrack
Command breakdown:
--wordlist=/word/list/path- Specifies the wordlist to use.--format=Format- Specifies the hash of the password to crack.FileToCrack- Specifies the file which contains the password to crack.
Using dictionary mode, John The Ripper will use a wordlist of potential passwords and generate the hashes for those passwords and compare them with our password hash. Dictionary mode will be the most common mode used when using John The Ripper.
For example, if we have the hash of a password using md5, we can save the hash to a file called hash.txt with the following contents:
e2e8f0bc2c1ec1de7ee50fbae3bfbd0f
Once done, we can use the following command to crack the hash using dictionary mode:
john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5 hash.txt
Command breakdown:
--wordlist=/usr/share/wordlists/rockyou.txt- Specifies the wordlist to use.--format=raw-md5- Specifies the hash format. In this example, md5.hash.txt- Specifies the file which contains the hash to crack.
Incremental Mode
Incremental mode example usage:
john -i:PW_LENGTH --format=FORMAT FileToCrack
Command breakdown:
-i:PW_LENGTH- Tells John The Ripper to use incremental mode with PW_LENGTH being how long you want the maximum number of characters in the passwords.--format=FORMAT- Specifies the format of the hash.FileToCrack- Specifies the file where the hash is saved to.
Using incremental mode, John The Ripper will try all possible character combinations as passwords. A downside when using this mode is when the password is sufficiently strong, it can take a long time for John The Ripper to crack the password.
For example, if we have a hash of a password that is in md5, we can save it to a file called hash.txt with the following contents:
e2e8f0bc2c1ec1de7ee50fbae3bfbd0f
Once done, we can use the following command to crack the hash using incremental mode:
john -i:5 --format=raw-md5 hash.txt
Command breakdown:
-i:5- Tells John The Ripper to use incremental mode with a max character length of 5.--format=raw-md5- Specifies the format of the hash. In this example, it will be md5.hash.txt- Specifies the file that contains the hash to crack.